Quantum computing, often hailed as the next frontier in technology, is a paradigm shift from classical computing. While classical computers use bits as the smallest unit of data, either a 0 or a 1, quantum computers use quantum bits, or qubits. These qubits can exist in a state of 0, 1, or both 0 and 1 simultaneously, thanks to the principle of superposition. This ability to be in multiple states concurrently allows quantum computers to process a vast amount of information at once.
| Aspect | Classical Computing | Quantum Computing |
|---|---|---|
| Basic Unit | Bit | Qubit |
| States | 0 or 1 | 0, 1, or both |
| Data Processing | Sequential | Parallel |
| Key Principles | Binary Logic | Superposition, Entanglement |
Another fundamental principle of quantum computing is entanglement. When qubits become entangled, the state of one qubit is dependent on the state of another, no matter the distance between them. This interconnectedness allows for faster and more efficient data processing.
The potential of quantum computing is vast. From revolutionizing drug discovery by simulating complex molecular structures to optimizing logistics in ways previously deemed impossible, the applications are endless. However, with great power comes great responsibility. The very principles that make quantum computing so promising also pose challenges, especially in the realm of data security and encryption.
Quantum Computing’s Potential Impact on Encryption
Encryption is the bedrock of modern digital security. From safeguarding our online transactions to protecting sensitive governmental data, encryption algorithms ensure that our digital lives remain private and secure. Classical computers, despite their power, find it challenging to break robust encryption schemes. However, quantum computers, with their unparalleled processing capabilities, pose a significant threat to these traditional encryption methods.
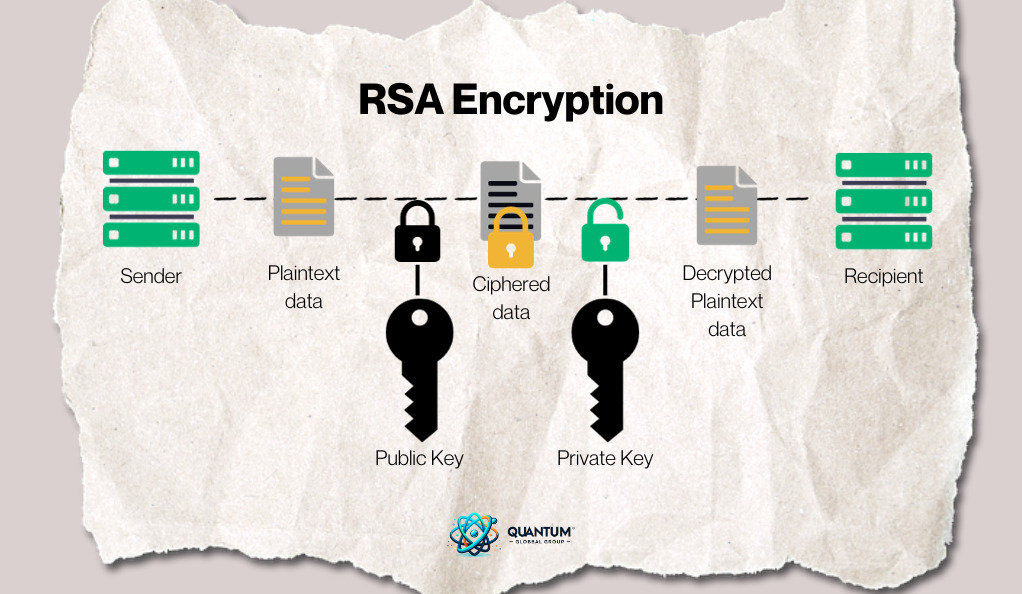
RSA Encryption: One of the most widely used encryption methods is the RSA algorithm, which relies on the difficulty of factoring large prime numbers. For classical computers, breaking RSA encryption by factoring these numbers is time-consuming, making it secure. However, a sufficiently powerful quantum computer could use Shor’s algorithm to factor these numbers exponentially faster, rendering RSA encryption vulnerable.
| Encryption Type | Classical Computing Security | Quantum Computing Threat |
|---|---|---|
| RSA | High (Time-consuming to break) | Vulnerable (Can be broken exponentially faster) |
| ECC (Elliptic Curve Cryptography) | High | Vulnerable (Shor’s algorithm can break it) |
| Symmetric Cryptography (e.g., AES) | High | Moderate (Quantum computers might require square root of the key size for brute force) |
The potential of quantum computers to break encryption doesn’t mean the end of digital security. Instead, it signifies the beginning of a new era: post-quantum cryptography. Researchers are already working on quantum-resistant algorithms that can withstand the power of quantum computers.
Legal Implications of Quantum Computing
The advent of quantum computing brings forth a plethora of legal challenges. Intellectual property (IP) is at the forefront of these challenges. As companies and researchers race to develop quantum technologies, questions about patent rights, trade secrets, and licensing agreements become paramount.
Intellectual Property in Quantum Tech: Quantum algorithms, hardware designs, and applications are all potential subjects for patents. However, the unique nature of quantum tech poses questions: Can quantum states be patented? How do we ensure that quantum algorithms are original, especially when superposition allows for multiple possibilities?
Moreover, with the global nature of quantum research, international IP laws come into play. Collaborations between countries and institutions can lead to disputes over ownership and rights. Clear legal frameworks are essential to navigate this uncharted territory.
Quantum Computing and Cybersecurity
The realm of cybersecurity is on the cusp of a significant transformation due to quantum computing. While the potential threats to encryption have been highlighted, it’s essential to understand that quantum computing isn’t just a challenge to cybersecurity but also a potential boon.
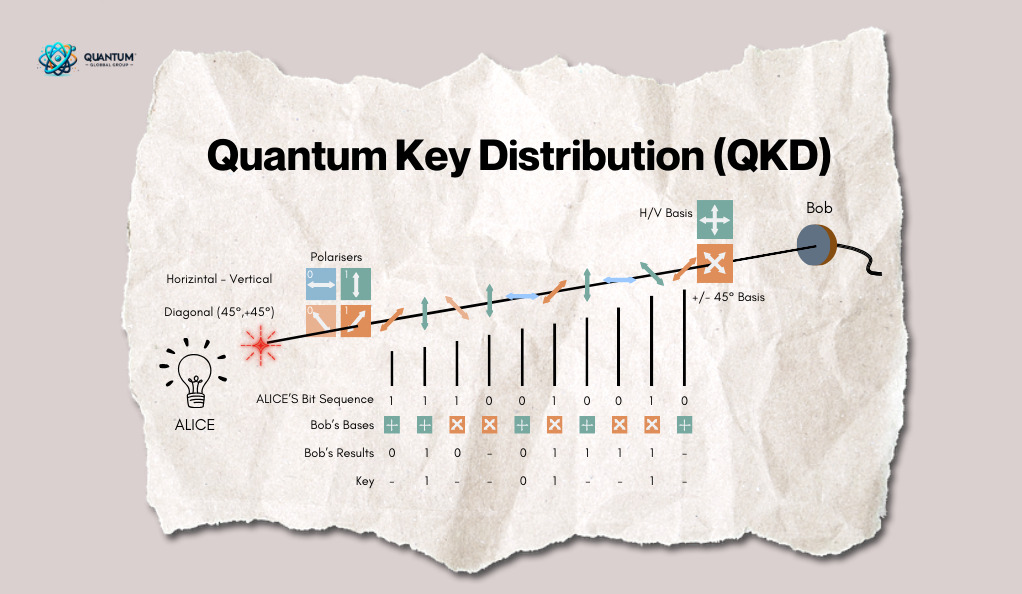
Quantum Key Distribution (QKD): One of the most promising quantum technologies in the context of security is Quantum Key Distribution. QKD uses the principles of quantum mechanics to create unhackable communication channels. Any attempt to eavesdrop on a quantum communication would disturb the quantum states being transmitted, making the intrusion detectable. This ensures a level of security that is theoretically unbreakable.
| Feature | Classical Cybersecurity | Quantum Cybersecurity |
|---|---|---|
| Key Distribution | Vulnerable to interception | Secure with QKD |
| Encryption Strength | Vulnerable to quantum attacks | Quantum-resistant algorithms in development |
| Intrusion Detection | Based on patterns and anomalies | Instantaneous due to quantum disturbance |
Ethical Considerations in Quantum Computing
As with any groundbreaking technology, quantum computing brings with it a host of ethical dilemmas. The sheer power of quantum computers means they could be used for both benevolent and malicious purposes.
Potential Misuse: In the wrong hands, quantum computers could be used for nefarious activities, from hacking into secure databases to manipulating financial markets or even weaponizing quantum technologies. The global community must be vigilant and proactive in establishing ethical guidelines for quantum research and application.
Balancing Innovation and Ethics: While it’s crucial to harness the potential of quantum computing, it’s equally important to ensure that its development doesn’t outpace our ethical considerations. Researchers, policymakers, and tech leaders must collaborate to create a framework that promotes responsible quantum innovation.
The Role of Governments and International Bodies
The global implications of quantum computing necessitate a coordinated response from governments and international organizations. Many countries have already recognized the strategic importance of quantum tech and are investing heavily in research and development.

International Collaboration: Given the universal nature of quantum challenges, especially in security and ethics, international collaboration is paramount. Joint research projects, shared standards, and mutual regulatory frameworks can ensure that quantum tech is developed responsibly and equitably.
Regulation and Oversight: As the quantum industry grows, there will be a need for regulatory bodies to oversee its development, ensuring that it adheres to ethical standards and doesn’t pose undue risks to global security.
Preparing for a Quantum Future: Legal Recommendations
As we stand at the precipice of a quantum revolution, the legal profession must be equipped to navigate the challenges and opportunities that lie ahead. The intersection of quantum computing and law is uncharted territory, and proactive measures are essential to ensure a harmonious coexistence.
1. Quantum Literacy for Legal Professionals: Understanding the basics of quantum computing is crucial for legal professionals, especially those in intellectual property, cybersecurity, and international law. Workshops, seminars, and courses can help bridge the knowledge gap.
2. Updating Legal Frameworks: Existing laws, especially those related to data protection, intellectual property, and cybersecurity, may not be equipped to handle quantum-specific challenges. Legislative bodies must revisit and revise these laws to ensure they are quantum-compliant.
3. International Quantum Agreements: Given the global nature of quantum challenges, nations should come together to draft international agreements on quantum research, ethics, and security. Such agreements can prevent potential conflicts and ensure collaborative progress.
4. Establishing Quantum Ethics Committees: To address the ethical dilemmas posed by quantum computing, institutions and governments should establish ethics committees. These committees, comprising experts from various fields, can provide guidance on responsible quantum research and application.
5. Encouraging Public-Private Partnerships: The development of quantum technology requires significant resources. Governments should collaborate with private entities, fostering an environment of shared research, innovation, and responsibility.
6. Fostering Transparent Quantum Research: Transparency in quantum research can prevent potential misuse and ensure that the broader community is informed about developments. Open-source quantum projects and public research journals can promote transparency.
7. Preparing for Quantum Litigations: As with any disruptive technology, quantum computing will likely lead to legal disputes, be it patent infringements, data breaches, or ethical violations. The legal profession must be prepared to handle such cases, ensuring that justice is served in this new quantum era.
Conclusion
The dawn of the quantum era heralds a transformative phase in human history. Quantum computing, with its unparalleled computational prowess, promises to reshape industries, redefine legal paradigms, and reimagine societal structures. From revolutionizing healthcare and finance to challenging our existing cybersecurity frameworks, the ripple effects of this technology are vast and far-reaching.
However, with immense power comes immense responsibility. As we stand on the cusp of quantum advancements, it’s imperative to approach this frontier with a balanced perspective. While the technological breakthroughs are undeniably exciting, they must be tempered with ethical considerations, legal foresight, and societal awareness. The challenges—be they in encryption vulnerabilities, intellectual property disputes, or ethical dilemmas—are as real as the opportunities.
In this journey into the quantum future, collaboration will be our compass. Governments, industries, academia, and civil society must come together to navigate the complexities of the quantum landscape. Through shared research, transparent dialogue, and proactive regulation, we can harness the power of quantum computing for the betterment of humanity.