In the realm of data security, the term “cryptography” often evokes images of secret codes, intricate algorithms, and impenetrable data fortresses. But as we venture deeper into the 21st century, a new player has emerged on the cryptographic stage: Quantum Cryptography. This revolutionary approach to securing information is not just a mere enhancement of classical cryptography; it’s a paradigm shift, leveraging the peculiarities of quantum mechanics to achieve levels of security previously thought impossible.
What is Quantum Cryptography?
Quantum Cryptography is the science of using quantum mechanical properties to perform cryptographic tasks. Unlike classical cryptography, which relies on mathematical algorithms and computational difficulty (like the challenge of factoring large numbers), quantum cryptography derives its strength from the fundamental principles of quantum mechanics.
Key Quantum Principles in Cryptography:
- Superposition: Quantum systems can exist in multiple states simultaneously. For example, a quantum bit or qubit can be both 0 and 1 at the same time, unlike classical bits which are either 0 or 1.
- Entanglement: Two or more quantum particles can become correlated in such a way that the state of one particle immediately affects the state of the other, no matter the distance between them.
- No-Cloning Theorem: It’s impossible to create an exact copy of an arbitrary unknown quantum state. This principle is particularly crucial for quantum key distribution, as eavesdroppers cannot clone quantum keys without detection.
- Wave Function Collapse: When a quantum state is measured, it collapses to one of its possible values, making eavesdropping detectable.
Why is Quantum Cryptography Important?
The advent of quantum computers poses a significant threat to classical cryptographic systems. Algorithms that would take classical computers millennia to crack could be solved by quantum computers in mere seconds. Quantum cryptography, however, stands resilient against such threats. The best-known example of quantum cryptography is quantum key distribution (QKD), which offers an information-theoretically secure solution to the key exchange problem. In simpler terms, it’s a method so secure that, theoretically, not even a quantum computer can breach it.
The Evolution of Quantum Cryptography
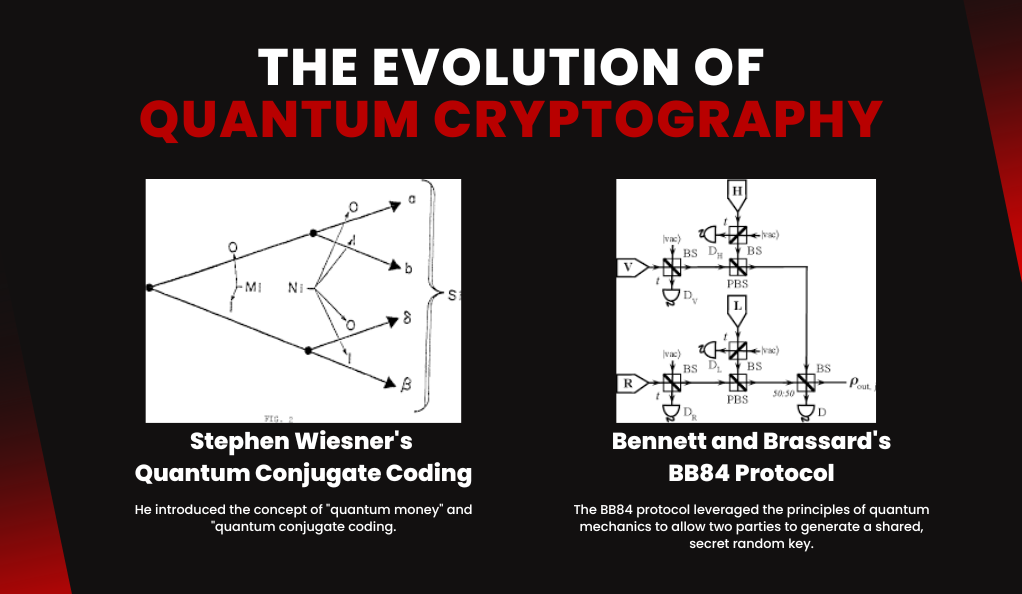
The journey of quantum cryptography is as fascinating as the quantum principles it’s built upon. From theoretical musings to real-world applications, the evolution of this field has been rapid and groundbreaking.
The Genesis: Stephen Wiesner’s Quantum Conjugate Coding
The seeds of quantum cryptography were sown in the early 1970s by Stephen Wiesner, then at Columbia University. He introduced the concept of “quantum money” and “quantum conjugate coding.” While the idea of quantum money (banknotes that couldn’t be counterfeited thanks to quantum mechanics) was revolutionary, it was his quantum conjugate coding that laid the groundwork for what we now know as quantum key distribution.
Bennett and Brassard’s BB84 Protocol
In 1984, Charles Bennett and Gilles Brassard proposed the BB84 protocol, the first and most well-known quantum key distribution (QKD) scheme. The BB84 protocol leveraged the principles of quantum mechanics to allow two parties to generate a shared, secret random key. The beauty of this protocol lies in its inherent security: if an eavesdropper tries to intercept the quantum keys, their presence becomes detectable due to the nature of quantum measurements.
From Theory to Practice: Real-world Implementations
The transition from theoretical concepts to practical applications was swift. By the early 2000s, several experimental QKD systems had been developed and tested over optical fibers and even free-space optical channels. These experiments proved that quantum cryptography could work outside of labs, paving the way for commercial quantum networks.
Milestones in Quantum Cryptography
| Year | Milestone | Significance |
|---|---|---|
| 1991 | Ekert’s QKD | Enhanced security through quantum entanglement. |
| 2004 | Vienna Bank Transfer | Demonstrated real-world application and commercial potential. |
| 2010 | Tokyo QKD Network | Integration into standard communication systems. |
Advantages of Quantum Cryptography
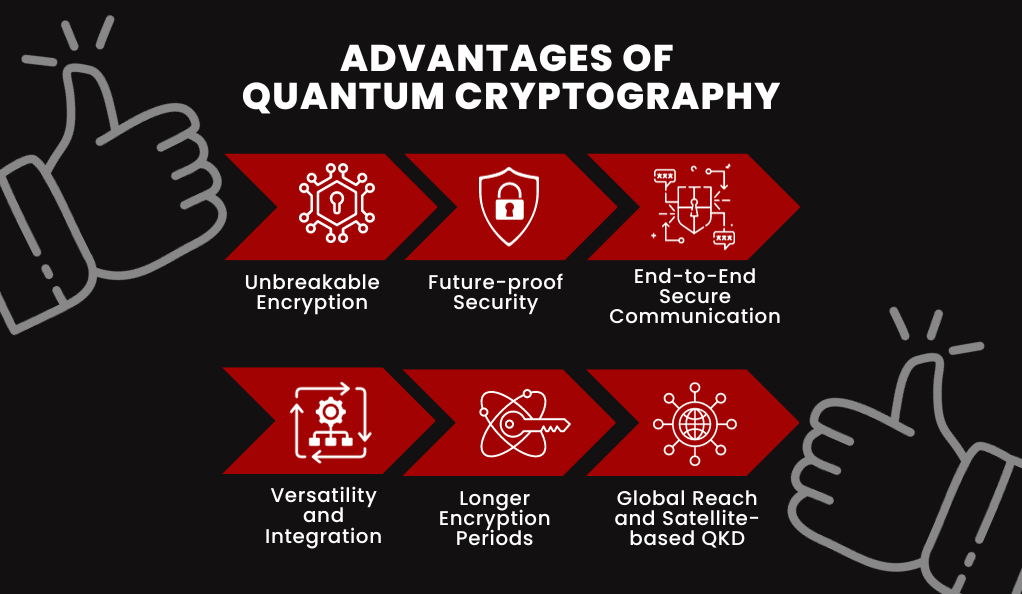
In the ever-evolving landscape of cybersecurity, quantum cryptography stands out as a beacon of unparalleled security. But what makes it so special? Let’s delve into the distinct advantages that set quantum cryptography apart from its classical counterparts.
Unbreakable Encryption
At the heart of quantum cryptography is the promise of unbreakable encryption. Thanks to the principles of quantum mechanics, any attempt to eavesdrop or intercept the quantum keys results in a disturbance that is immediately noticeable. This means that any potential breach can be detected and addressed in real-time, ensuring the integrity of the communication.
Future-proof Security
With the imminent arrival of quantum computers, many classical cryptographic methods are at risk. Quantum computers can, in theory, break widely-used encryption algorithms in mere seconds. Quantum cryptography, however, remains impervious to such threats. Its security doesn’t rely on computational difficulty but on the fundamental laws of physics, making it resistant to even the most powerful quantum computer attacks.
End-to-End Secure Communication
Quantum Key Distribution (QKD) allows two parties to establish a shared secret key that can be used for encrypting and decrypting messages. This key is generated in such a way that it’s known only to the communicating parties, ensuring end-to-end secure communication. If any third party tries to intercept the key, the quantum system will show signs of disturbance, alerting the parties involved.
Versatility and Integration
Modern quantum cryptographic systems are designed to be compatible with existing communication infrastructures. This means that they can be integrated into current systems without the need for a complete overhaul, making the transition to quantum-secure communications smoother and more cost-effective.
Longer Encryption Periods
Quantum cryptographic keys have the potential for longer encryption periods. While classical keys might need frequent changing to maintain security, quantum keys, due to their inherent security features, can remain effective for more extended periods, reducing the overhead of key management.
Global Reach and Satellite-based QKD
Recent advancements have seen the successful demonstration of satellite-based QKD, allowing for secure quantum communications over global distances. This breakthrough paves the way for a global quantum-secure communication network.
Practical Applications and Protocols
While the theoretical underpinnings of quantum cryptography are undoubtedly fascinating, its real value emerges when we examine its practical applications and the protocols that make these applications possible.
Quantum Key Distribution (QKD)
As previously mentioned, QKD is the most well-known application of quantum cryptography. It allows two parties to generate a shared, secret random key. The key can then be used to encrypt and decrypt messages, ensuring secure communication.
BB84 Protocol
The BB84 protocol, introduced by Bennett and Brassard, remains the cornerstone of QKD. It uses two sets of orthogonal quantum states to transmit bits. The security of the protocol arises from the no-cloning theorem: an eavesdropper cannot make a perfect copy of the quantum states without disturbing them, making eavesdropping detectable.
Ekert91 Protocol
Developed by Artur Ekert in 1991, this protocol uses entangled quantum states for key distribution. The security here is based on the violation of Bell inequalities, providing a different approach to ensuring secure communication.
Quantum Digital Signatures
Just as digital signatures in classical cryptography provide authentication and non-repudiation, quantum digital signatures offer the same but with the added security features of quantum mechanics. They ensure that a message has not been tampered with and verifies the identity of the sender.
Quantum Secure Direct Communication (QSDC)
QSDC is a cryptographic protocol that allows the direct transmission of secret messages without the need for a key exchange. The security of QSDC is based on the principles of quantum mechanics, ensuring that the direct communication remains confidential and secure.
Quantum Cryptographic Protocols for Secure Multi-party Computation
In scenarios where multiple parties need to compute a function over their inputs while keeping those inputs private, quantum cryptography offers protocols that ensure security against potential eavesdroppers. These protocols are especially valuable in areas like secure voting, auctions, and contract signing.
Applications in Various Sectors
- Banking and Finance: Quantum cryptography can secure financial transactions, ensuring that funds transfers, digital payments, and online banking activities remain confidential and tamper-proof.
- Healthcare: With the increasing digitization of medical records, quantum cryptography can play a pivotal role in ensuring the privacy and security of sensitive patient data.
- Defense and Military: In an era of cyber warfare, quantum-secured communication can protect critical military data, strategies, and communications from potential adversaries.
- Telecommunications: As the backbone of global communication, the telecom sector can benefit immensely from quantum cryptography, ensuring secure communication channels worldwide.
Mistrustful Quantum Cryptography
In the intricate dance of cryptography, trust plays a pivotal role. However, what happens when parties inherently distrust each other? Classical cryptography has its limitations in such scenarios, but quantum cryptography offers intriguing solutions. Let’s delve into the world of mistrustful quantum cryptography.
Understanding Mistrust in Cryptography
In many cryptographic scenarios, parties may not trust each other but still need to collaborate or exchange information. These situations require cryptographic protocols that can function effectively even in the absence of mutual trust.
Quantum Commitment Schemes
Commitment schemes are fundamental cryptographic primitives where one party commits to a value while keeping it hidden from the other, revealing the value later. In a quantum setting, these schemes leverage quantum mechanics to ensure that once a party commits to a value, they cannot change it without detection.
Quantum Coin Flipping
Imagine a scenario where two distant parties want to flip a coin, but neither trusts the other to do it fairly. Quantum coin flipping allows this to happen with the assurance that neither party can cheat significantly. The protocol uses quantum superposition and entanglement to ensure fairness.
Quantum Oblivious Transfer
Oblivious transfer is a protocol where one party sends information to another, but remains oblivious about what part of the information the other party received. Quantum oblivious transfer leverages the principles of quantum mechanics to achieve this, ensuring that the sender remains unaware of the receiver’s choice, and the receiver only gets the information they chose.
Quantum Bit Commitment
In this protocol, a party commits to a bit value without revealing it, and later, they can unveil the committed bit. The quantum nature ensures that once committed, the bit cannot be changed, and until unveiled, it remains hidden from the other party.
Applications in Real-world Scenarios
- Secure Auctions: In a mistrustful setting like an auction, quantum cryptographic protocols can ensure that bids remain confidential and tamper-proof until the auction’s conclusion.
- Voting Systems: Quantum cryptography can be employed in electronic voting systems to ensure that votes remain anonymous and cannot be altered, even if parties distrust the voting authority.
- Contract Signing: In situations where parties may not trust each other but need to sign a contract, quantum protocols can ensure that neither party can cheat the other during the signing process.
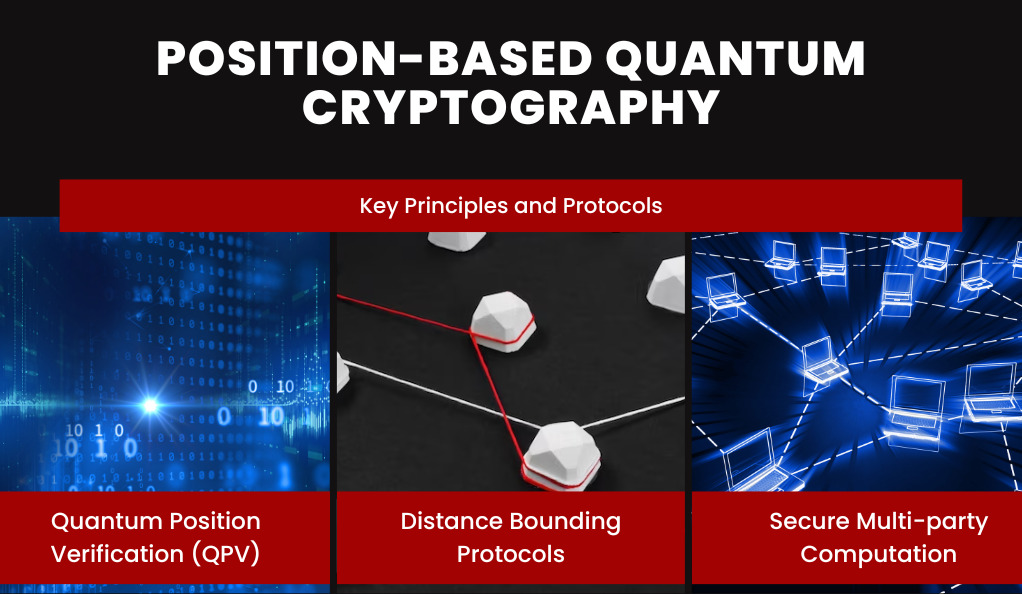
Position-based Quantum Cryptography
In the vast spectrum of cryptographic techniques, position-based quantum cryptography stands out as a unique and innovative approach. Here, the very geographical location of a participant becomes a crucial element in the cryptographic process. Let’s delve deeper into this intriguing domain.
The Concept of Position-based Cryptography
Traditionally, cryptographic protocols rely on secret keys or specific algorithms to ensure security. However, in position-based cryptography, the emphasis shifts from “what you know” or “what you have” to “where you are.” The central idea is to use a participant’s geographical location as a cryptographic credential.
Why Quantum Mechanics?
While the concept of position-based cryptography isn’t inherently quantum, classical schemes are vulnerable to “man-in-the-middle” attacks. Quantum mechanics, with its unique properties like no-cloning and entanglement, offers a robust framework to make position-based cryptography secure against potential adversaries.
Key Principles and Protocols
- Quantum Position Verification (QPV): The primary protocol in position-based quantum cryptography. It allows a verifier to confirm the position of a prover by sending quantum signals and expecting a response within a certain time frame, considering the speed of light.
- Distance Bounding Protocols: These protocols ensure that a participant is within a certain distance from a reference point. Quantum versions of these protocols leverage the principles of quantum mechanics to achieve higher levels of accuracy and security.
- Secure Multi-party Computation: In scenarios where multiple parties, located at different geographical locations, need to compute a function over their inputs, position-based quantum cryptography can ensure that the computation is done securely, considering the positions of all participants.
Conclusion
In the ever-evolving landscape of technology, quantum cryptography stands as a testament to the profound influence of quantum mechanics on data security. As we transition into a quantum-ready world, the fusion of quantum principles with artificial intelligence heralds a future of unparalleled computational prowess and security. Industries, governments, and academia are collaboratively pushing the boundaries, preparing for a future where quantum-enhanced solutions become the norm.
Richard Feynman’s assertion that nature is inherently quantum resonates now more than ever, reminding us of the limitless possibilities that await in the quantum era. As we conclude, it’s evident that the quantum revolution, with its blend of mystery and promise, is reshaping our digital world, ushering in a future rich with potential and innovation.